High-Tech Bridge Free SSL Server Tester
What is High-Tech Bridge Free SSL Server Tester?
✍: FYIcenter.com
![]() High-Tech Bridge Free SSL Server Tester
is an online tool that checks a specified Website
to see if its SSL/TLS certificate is installed correctly or not.
High-Tech Bridge Free SSL Server Tester
is an online tool that checks a specified Website
to see if its SSL/TLS certificate is installed correctly or not.
You can follow these steps to try High-Tech Bridge Free SSL Server Tester:
1. Go to https://www.htbridge.com/ssl/.
2. Enter the URL of the Website you want to check, for example, www.visa.com.
3. Click "Submit" icone. You will see the output of the test:
Summary of www.visa.com SSL/TLS Security Test:
FINAL GRADE: A COMPLIANT WITH PCI DSS: Pass HOST: 23.66.183.137:443 The server configuration seems to be good, but is not entirely compliant with NIST guidelines The server prefers cipher suites supporting Perfect-Forward-Secrecy
SSL Certificate Overview:
Common Name - www.visa.com
subjectAltName - DNS:promocoesvisa.com.br, DNS:www.visa.ca, DNS:visa.com, ...
Country - US
State or province - California
Locality- - Foster City
Organization - Visa International Service Association
Organization Unit - Web Services
basicConstraints - CA:FALSE
keyUsage - Digital Signature, Key Encipherment
crlDistributionPoints - Full Name: URI:http://gn.symcb.com/gn.crl
certificatePolicies - Policy: 2.23.140.1.2.2 CPS: https://www.geotrust.com/resources/repository/legal
extendedKeyUsage - TLS Web Server Authentication, TLS Web Client Authentication
authorityKeyIdentifier - keyid:D2:6F:F7:96:F4:85:3F:72:3C:30:7D:23:DA:85:78:9B:A3:7C:5A:7C
authorityInfoAccess - OCSP - URI:http://gn.symcd.com CA Issuers - URI:http://gn.symcb.com/gn.crt
Certificate Transparency - jhvz O hp~.=TG0EpSh-{QQirr p6oO ,-3=eSiRj _~v Xgp 5w TG0EN[u7=gDY.4 ,gqq6JMpvhd:(LqQ]gD gOOTG0E S|r3o1NIb1}yu;I9 O5*
Key type - RSA
Key size - 2048 bits
The Certificate Signature Algorithm - sha256WithRSAEncryption
Issuer - GeoTrust SSL CA - G3
Not Before - 2016-05-27 02:00:00 UTC.
Not After - 2017-08-27 01:59:59 UTC.
Test for Compliance with NIST Guidelines:
SUPPORTED ELLIPTIC CURVES
P-256 (prime256v1) (256 bits)
SUPPORTED PROTOCOLS
TLSv1.0
TLSv1.1
TLSv1.2
SUPPORTED CIPHERS
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
SERVER DOES NOT SUPPORT OCSP STAPLING
The server does not support OCSP stapling. Its support allows better
verification of the certificate validation status.
Non-compliant with NIST guidelines
Test for Compliance with PCI DSS Requirements:
SUPPORTED ELLIPTIC CURVES
P-256 (prime256v1) (256 bits)
SUPPORTED PROTOCOLS
TLSv1.0
TLSv1.1
TLSv1.2
SUPPORTED CIPHERS
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
POODLE
The server is not vulnerable to POODLE over TLS.
CVE-2016-2107
The server is not vulnerable to OpenSSL padding-oracle flaw (CVE-2016-2107).
SERVER DOES NOT SUPPORT CLIENT-INITIATED INSECURE RENEGOTIATION
The server does not support client-initiated insecure renegotiation.
HEARTBLEED
The server version of OpenSSL is not vulnerable to Heartbleed attack.
CVE-2014-0224
The server is not vulnerable to CVE-2014-0224 (OpenSSL CCS flaw).
Test for Industry Best-Practices:
CERTIFICATE IS NOT EV
The certificate is NOT an Extended Validation (EV) certificate.
SERVER SUPPORTS TLSv1.2
The server supports TLSv1.2 which is the only SSL/TLS protocol that
currently has no known flaws or exploitable weaknesses.
SERVER PREFERS PFS ENABLED CIPHER SUITES
For TLS family of protocols, the server prefers cipher suite(s)
providing Perfect Forward Secrecy (PFS).
HTTP SITE DOES NOT REDIRECT
The HTTP version of the website does not redirect to the HTTPS version.
We advise to enable redirection.
SERVER DOES NOT PROVIDE HSTS
The server does not send the HTTP-Strict-Transport-Security. We advise
to enable it to enforce the user to browse the website in HTTPS.
SERVER DOES NOT PROVIDE HPKP
The server does not send HTTP-Public-Key-Pinning header. We advise
to enable HPKP in order to avoid Man-In-The-Middle attacks.
SERVER SUPPORTS TLS FALLBACK SCSV EXTENSION
The server supports TLS_FALLBACK_SCSV extension for protocol downgrade
attack prevention.
SERVER SUPPORTS CLIENT-INITIATED SECURE RENEGOTIATION
The server supports client-initiated secure renegotiation which may
be unsafe and allow Denial of Service attacks.
SECURE RENEGOCIATION SUPPORTED
The server supports secure server-initiated renegotiation.
TLS COMPRESSION SUPPORT
TLS compression is not supported by the server.
SERVER PREFERRED CIPHER SUITES
Preferred cipher suite for each protocol supported (except SSLv2).
Expected configuration are ciphers allowed by PCI DSS and enabling PFS:
TLSv1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLSv1.1 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLSv1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
Web Server Security Overview:
Overview
Your grade for web server security is "F".
This test doesn't impact your SSL/TLS score.
Tested URL - https://www.visa.com
Redirect To -
Server Signature - AkamaiGHost
HTTP Response - 200 OK
HTTP Methods Overview
HTTP methods (or verbs) that are allowed by the server. Some may
be dangerous if not handled properly by the application.
GET
POST
HEAD
OPTIONS
DELETE
PUT
TRACE - Should not be allowed
HTTP Headers Overview
Overview of HTTP headers sent by the server. These headers are known
to improve security for your visitors.
Server
Strict-Transport-Security - The header was not sent by the server.
Public-Key-Pins - The header was not sent by the server.
X-Frame-Options - The header was not sent by the server.
X-XSS-Protection - The header was not sent by the server.
X-Content-Type-Options - The header was not sent by the server.
Content-Security-Policy - The header was not sent by the server.
Cookies Overview
No cookies were sent by the web application.
Surprisingly, www.visa.com gets a "F" on Web Server Security.
The picture below shows you High-Tech Bridge Free SSL Server Tester output on www.visa.com:
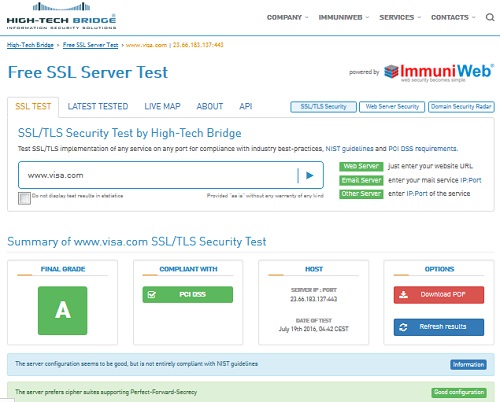
⇒ High-Tech Bridge Free SSL Server Tester Failed Example
⇐ Server Certificate Online Tools
2016-10-08, ∼4015🔥, 0💬